Sunday, April 24, 2016
Mobile Device Privacy Battle in the US - Forgetting is Easy - Deleting is Hard
Monday, February 27, 2012
Testola
As you can see above, it works quite well. It works even more easily in Google Sites, where you can navigate through the user interface to the specific Google Doc, Chart, or whatever you want to show without inserting any code. The only caveat is that you have to change the permissions on that doc to make it accessible. Otherwise, it is only visible when someone you explicitly share the document with has signed into their account.
Thursday, August 25, 2011
BBM Music - If you can't compete, lock your customers in
Saturday, May 14, 2011
Chromebook Please
Thursday, April 28, 2011
On-line Security, They Told You So
Thursday, December 16, 2010
High Hopes for ChromeOS
1) What is it?
2) Why should I care?
I can address #1 somewhat. ChromeOS is an operating system Google is making available to partner computer manufacturing companies that boots straight into the Chrome Web Browser and really restricts itself to using the web. The concept is that people using netbooks and even full-power laptops and desktops often spend the majority of their time in the web browser. Google has improved the Chrome Web browser, incentivized web app developers by adding a web app store, simplified the operating system to running this single application, baked in the latest security capabilities in a user-friendly fashion, and dictated inclusion of up-to-date wifi and 3G radios in the hardware so that users can be almost always connected.
So, why should you care? Google partially answers that question here:
http://www.youtube.com/watch?v=lm-Vnx58UYo
For myself, manufacturers should be able to turn this platform into cheap, simple to use, long battery-lived, quick access computers that do nearly all the things people do on today's computers and more. Powerful applications can run on powerful servers instead of requiring you to lug around beefier hardware. Simple applications stay simple, are always up to date, and don't expose your data to loss or theft when, inevitably, the computer is damaged or lost. The frustrating days of paying thousands of dollars for a laptop, then hundreds or thousands more for applications, loading it up with private info, personally owned media, and precious memories, only to leave it in the airport security line and lose everything may soon be behind us.
Google's CR-48 pilot program demonstrates all these benefits for some, however, access to them remains in the future for the larger marketplace. Google's pilot program demonstrates what can be done but its up to other parties to carry this forward. Manufacturers need to come out with compelling hardware at a reasonable price, soon. Developers need to leverage the power of HTML5 in their web apps to make them perform like locally-installed apps. More web development of private cloud technology is necessary so that people and businesses have a secure place to keep their info that doesn't belong to a third party. Finally, wireless carriers need to get on-board. Nobody wants yet another 2 year, $60/month contract tied to a single, limited device. I really don't want to pay by the byte, either, (would you want to pay for your electricity by the electron?) but that appears to be the way things are headed. The 100MB/month free setup Verizon includes with Google's CR-48 pilot program is encouraging but it remains to be seen what will be offered with real products. Here's hoping it all comes together
Wednesday, December 1, 2010
Why Is My Home WiFi Flaky?


Don't Get Me an Internet TV Device for Christmas

Thursday, September 23, 2010
Windows Home Server and Apple Time Capsule
I'm in the middle of backing up all my systems (two Windows laptops, an older desktop, and a Mac Mini) to the server at the moment so I haven't messed with it. So far, the system has performed well. A few warnings, though:
1) The Media Collector that comes with the HP-branded models works great for automatically collecting and organizing music from iTunes. Some sites claim it does the same thing for videos from iTunes and photos from iPhoto. That hasn't been the case in my first 24 hours of experience. iPhoto's approach of storing everything together along with a DB only it can manage doesn't lend itself to sync with any other system and HP's software is no exception. Since we switched to using Picasa a while ago, which uses the approach of leaving image files where they are and detecting new ones as they arrive, our more recent photos have synced over but the old ones from iPhoto have not. I'm not sure what to think about the iTunes movies. Its amazing what the Mediasmart Server does, but it doesn't quite meet the expectations I had, so far.
2) The point of the Media Collector is gathering all your media together from different systems. You get out of this process, however, what you put into it in terms of organizing your media before the collector goes to work. Again, in contrast to its nice handling of music, photos and movies are collected into the server shares by username. Unless you happen to use the same account on all your systems with similar folder structures and everything it its default location (e.g. all your pictures you want collected in the windows "My Pictures" folder), Collector makes an equivalent mess out of your files in its shares. One option I found out about too late is enabling the Guest account on the server. This option should allow everything to be Collected under that single username.
Friday, August 6, 2010
WSJ and re-reporters miss point on IE In-private Filter
Despite the WSJ's extensive documentation of Microsoft's internal wrangling, this story about Microsoft "quashing" their In-Private filter sounds trumped-up and hypocritical of the other browser companies. IE8's InPrivate Filtering is comparable to Google Chrome's Incognito Mode (lovingly known as "Porn mode") feature. Neither of them have the setting stick - you have to manually enable it with every launch of all browsers on the market (and Mozilla's Firefox followed suit with version 3.5 later in 2009).
MS enables essentially the same feature in the same way - late to the market, as usual - and suddenly, over a year later, the WSJ is crying foul because Microsoft also does online advertising on the side. Did everyone forget that Google is the world's biggest online advertising company? The only news here is how long after Apple and Google released private browsing it took MS to release the same feature in IE8. MS has certainly played catch-up with IE8 but they have no greater conflict of interest than their competitors. In fact, I'd say Google has a far greater conflict of interest with Chrome since they purchased Doubleclick, the world's largest online ad tracking service at the time. Google passed up the same opportunity to do something potentially good for the consumer by making private browsing the default.
Monday, July 19, 2010
Apple Apologizes Reluctantly for iPhone 4 Antenna Problems, Blames Media, No One Explains Problem Plainly
Thursday, June 10, 2010
User-focussed mobile data plan model
It is easy to criticize, however, and hard to propose a more reasonable alternative. The fact is that carriers are saying they will provide feedback to users about how much data they have "used" along with warnings when they're about to exceed the plan amount. Also, bytes, like minutes for phone plans (as in, used for talking), are fairly easy for users to understand and carriers to monitor. The more data you send and receive, the more you pay. Carriers, for their part, need to track usage as part of normal operations to ensure their network is balanced, anyway, so why not report those data to users. Its simple, in concept. How else should usage be tracked if not by byte?
So, what if we came up with a way to meter the bill based on something that's focussed on user experience? The primary complaints customers have, and the primary challenges of a carrier, are capacity and availability. If there are great connections all over a city but poor connections outside the city, what happens when you're driving or taking the train home for the evening? Your call gets dropped and your files start downloading slowly. So, why should you pay the same price while you're in a bad area as you do in a good area? Reversing the scenario, what load (and therefore cost to the carrier) do you put on the network when you're in an office building where the signal doesn't penetrate? How about when your phone is powered off? None. The carrier allocates zero wireless capacity resources to you when you're off the grid. So, why should you be paying at all for the significant portion of the day when you're not able to use the service? I suggest billing based on two factors: 1) The Carrier's quality of service to the user (i.e. speed and latency) and 2) The portion of time that service is available to the user (availability). The better job the Carrier does, the greater proportion of the plan fee they can charge their customer at the end of the month.
As with any idea, the implementation details determine everything. I'm not advocating making the wireless business so volatile that carriers can hardly stay in business. Reasonable limits should be in place such that customers have a minimum fee to pay, even if they choose to turn their phone off all month. There are some costs to having the network available to you, even if you don't choose to use it. Likewise, reasonable limits should be in place on how much the carrier can charge if they achieve 99.99% coverage, quality, and reliability. That maximum amount should be known and agreed to when the plan is purchased. Carriers should publish their quality and reliability numbers, by area, every month with history reported for at least the length of the longest contract offered, so that customers can make informed choices when selecting their carrier.
This approach has merits for the customer in that it re-balances power such that more is in hands of customers and it gives carriers an immediate and continuing incentive to improve the customer experience. It also gets the industry away from billing customers for a commodity that has no direct link to cost - bytes - and which customers have little to no control over (web pages don't tell you how big they are before you load them!). Instead, the industry moves towards billing for the primary cost drivers - capacity and availability. Carriers who provide a better experience by expanding and balancing their networks better make more money. Customers pay for availability at an agreed quality level.
Tuesday, June 8, 2010
Apple WWDC 2010 Keynote Video available as a Podcast, too
Friday, June 4, 2010
Friendship isn't binary
Another thought on what turns me off about Facebook: it treats friendship as if its binary. You are either friends with someone or you are not. No matter how much time you spend messing. With your privacy settings, even at its most locked down, annyone marked as a friend sees everything. What about family, acquaintences, work buddies, neighbors, or those true friends who help you move (bodies)? They're all lumped together into an on or off, up or down, in or out world. So, users must either constantly filter what they say for the current (and future) mix of ins or, as I'd guess everyone with more than 10 or so friends does, post whatever and forget about the consequences. Without any sense of groups of friends, you may as well make everything public. This approach simply doesn't fit my life.
Thursday, June 3, 2010
Mac Malware in the wild, finally?
http://news.cnet.com/8301-27080_3-20006502-245.html?part=rss&tag=feed&subj=News-Security
It appears to have been caught very quickly at the sites where it was available for download and its spread limited. It also appears to be highly adaptable. This is nowhere near as virulent as the horror stories of infection on Windows PCs by simply opening an e-mail (without opening the attachment) or visiting a website (without knowingly downloading anything). With Apple touting "no viruses and spyware" as a feature for the past several years, however, Mac users may be less suspicious and less prepared to deal with this type of threat. In this case, a user has to download and install a program that is advertised for a different and quite useful purpose from a trusted download site. Then the software downloads and installs the truly malicious code without the user's knowledge. The truly weak links, here, are the sites (Softpedia, MacUpdate, and VersionTracker) where the malicious download was allowed to be made available. If you can't trust these sites, some of the biggest names in free software download, who can you trust?
Friday, May 14, 2010
Not impressed with the quality of this BlackBox Server Enclosure
would turn into a shop project? Even though APC, who shipped rack
rails with the UPS, and BlackBox, who makes the rack enclosure, both
claim to use #10-32 screws, I was only able to make APC's screws fit
in about 1/10 holes in BlackBox's rack. Other screws of this size from
lab supply didn't fare any better. Luckily, we have a whole pile of
BlackBox screws that came with the enclosure. Their own screws fit in
about 1/2 the threaded holes in their own rack. It took a powered
driver to get them all in, too, sometimes taking multiple tries to get
part of the way in, back out and blow off all the metal shavings, then
go a little farther.
Like I said, I'm not impressed BlackBox.
I am Deactivating then Deleting my Facebook Account
Goodbye Facebook. The evidence is overwhelming. Facebook has proven itself unworthy of my trust with even the little personal information I have chosen to share with it (basically a name, picture, and e-mail address. As soon as I figure out how to do it, I will be deleting my account. Seriously, they don't make it easy. There are instructions here: http://www.wikihow.com/Permanently-Delete-a-Facebook-Account
I'm tired of blocking/ignoring app requests because Facebook passes my contact details to whoever owns the app (not identified), not just my friends. Who wants more spam? I'm tired of trying to dig through the mounting pile of privacy settings just to do what I came on here to do: Communicate with you - my friends and family - and only you.
Here's a timeline of Facebook terms of service changes relating to Privacy up to Dec 2009: http://www.eff.org/deeplinks/2010/04/facebook-timeline/
Here's a more visual representation of how the default settings have made more and more of our personal information public:http://www.huffingtonpost.com/2010/05/07/facebook-privacy-changes_n_568345.html
The more recent changes in April extend to following me around the web and sharing even more of what I do, say, and what you say about me (which may reveal more personal info than I had intended) with third party companies. Facebook's response to user questions and complaints in an interview with the New York Times -http://bits.blogs.nytimes.com/2010/05/11/facebook-executive-answers-reader-questions/ - unapologetically says "Everything is opt-in on Facebook. Participating in the service is a choice." That's very interesting spin. It means, by having a Facebook account, I "opt-in" by default to all the poorly-explained personal information sharing that Facebook wants to do and may want to expand into in the future. Details about their recent changes are all over the web but are also so confusing that it's not worth the time for the limited functionality I get from Facebook. So, I'm taking their advice and opting-out the only feasible way Facebook now offers.
If you would like to stay connected with me, you can find me at my personal blog - http://agcrazylegs.blogspot.com/ - where I know what the rules are and you probably already have my e-mail address, chat logons, twitter account, or some other way to reach me.
If not, take care. It was nice catching up. Perhaps the next Livejournal/Friendster/MySpace/Facebook iteration will be better. Perhaps open, federated standards for identity online will become both available and useful one day soon. Perhaps we'll meet again.
I'm tired of blocking/ignoring app requests because Facebook passes my contact details to whoever owns the app (not identified), not just my friends. Who wants more spam? I'm tired of trying to dig through the mounting pile of privacy settings just to do what I came on here to do: Communicate with you - my friends and family - and only you.
Here's a timeline of Facebook terms of service changes relating to Privacy up to Dec 2009: http://www.eff.org/deeplinks/2010/04/fac
Here's a more visual representation of how the default settings have made more and more of our personal information public:http://www.huffingtonpost.com/2010/05/07
The more recent changes in April extend to following me around the web and sharing even more of what I do, say, and what you say about me (which may reveal more personal info than I had intended) with third party companies. Facebook's response to user questions and complaints in an interview with the New York Times -http://bits.blogs.nytimes.com/2010/05/11
If you would like to stay connected with me, you can find me at my personal blog - http://agcrazylegs.blogspot.com/ - where I know what the rules are and you probably already have my e-mail address, chat logons, twitter account, or some other way to reach me.
If not, take care. It was nice catching up. Perhaps the next Livejournal/Friendster/MySpace/Facebook iteration will be better. Perhaps open, federated standards for identity online will become both available and useful one day soon. Perhaps we'll meet again.
Friday, January 29, 2010
User Comfort with a Limited Device
Thursday, January 28, 2010
iPad - Its the coffee-table book of computers
Wednesday, September 16, 2009
Testing Windows Live Writer
So, I’m using Windows Live Writer to write this post. I’m not sure why and especially why now. I guess I just felt like writing and wanted to try out what I’d heard was a nicer interface. Despite MS’s “System Requirements” saying the minimum screen resolution is 1024x768, this looks fine on my netbook at 1024x600:
Okay, scratch that, some of the GUI elements are hidden due to the low resolution. For example, see the nearly hidden button at the bottom of the picture pane, here:
Luckily, Asus’s EEEPCs come with software to squish 768 virtual vertical pixels into 600 actual vertical pixels. Its not perfect but it does the job. I’m guessing from the software’s “About” screen that I’m not using the Beta version:
So far, I like it. Sometimes a web page editing interface just feels clunky. Even Google’s pages on Google’s Chrome Browser can feel less interactive than they should, especially on such low-end hardware.
Monday, March 9, 2009
The data business
Friday, October 31, 2008
Securing your Wireless network with XP systems, Step 3 of 3
This part has already been detailed elsewhere. Go see the "Configure WPA-PSK on Windows XP" section of this page:
http://www.microsoft.com/windowsxp/using/networking/expert/bowman_03july28.mspx
Securing your Wireless network with XP systems, Step 2 of 3
- Step 2 – Configure your wireless router to use WPA
Go to your desktop machine that’s plugged in to the network (not wireless). Point your browser at http://192.168.1.1 which is the default address for most Linksys routers. This is the configuration page for your router, not some website on the internet.
A box asking for your password should pop up, like this:
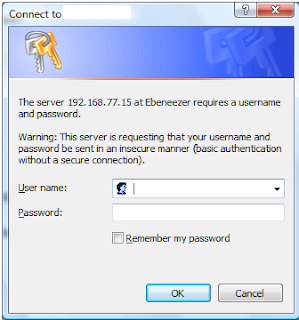
Leave the User name blank. If you’ve set a password, enter it. Otherwise, the default password on linksys routers is usually: admin
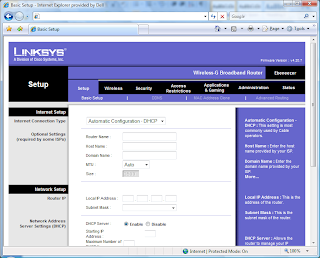
You’ll get into the router’s opening screen, which looks like this:
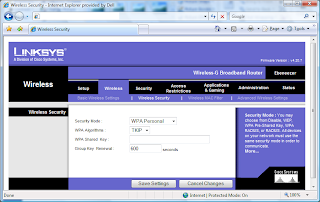
At the top of the page, click on “Wireless” and then “Wireless Security in the tab below it. Choose settings and a strong “WPA Shared Key”, like this:
If you really want a strong key that will drive everyone nuts, go to this web page: https://www.grc.com/passwords.htm
Regardless, make sure to paste a copy of your “WPA Shared key” into a text file and save it on your desktop computer. A handy way to get this key to your laptops is to copy that file to a USB stick if you have one handy.
Then click Save Changes at the bottom of the page and your router’s good to go.
Securing your Wireless network with XP systems, Step 1 of 3
You can tell if your XP system has the updates by right clicking on "My Computer" (located on the Desktop or Start Menu) and choosing "Properties." You'll see a screen pop up that looks like this:
from http://helpdesk.gwu.edu/security/images/winver.xp.gif
Note the "Service Pack #" listed under "System."
-If the number is 2 or 3, then your system is up to date with WPA compatibility.
-If its 1 or not there at all, I strongly recommend going to http://windowsupdate.microsoft.com and installing the latest service pack. Otherwise, you're leaving yourself wide open to all sorts of vulnerabilities that MS fixed in those Service Packs and you probably shouldn't be connected to the internet.
Why I Insist on Securing Networks
***Steps up on soap box***
See this article for an example of why I insist on securing networks when folks ask for my help or opinion.
http://www.dailytech.com/
The summary is that an elderly couple was recently threatened to pay over $800 to avoid being sued for illegally distributing a racing video game. The threat was based solely on evidence that their network IP address was involved in the file share. In this case, the charges were dropped when enough bad publicity occurred since the couple was obviously not involved. It was not reported exactly how their network IP address was used in the alledged illegal activity.
One way this problem could occur is if the couple had an unsecured wireless router and a nearby irresponsible or malicious individual decided to switch to their network. That individual could be a neighbor or could be someone who parked out at the curb with a laptop for a few minutes. If its your network, whatever that person does becomes your problem because it points back to the IP address your Internet Service Provider (ISP) assigned to you. ISPs are required to log which customer had which IP address at what times and they willingly provide that information when requested by litigious companies. ISPs generally do not risk getting sued themselves to protect their customers. Lock your wireless network down with Wireless Protected Access (WPA) and a strong password, and you can't be exploited this way.
***Steps down off soap box***






